As I wrote on my recent post here, I was involved into a project to implement a Meraki MX into the Azure Cloud. This project also includes a migration phase with site-to-site VPN tunnels between Meraki MX and Cisco ASA.
Even if the “Non-Meraki VPN peers” are supported on the Meraki MX, you may have some surprises with the Cisco ASA. Here are some tips to avoid problems and save you time.
The tests below have been made with MX version 14.31 (in beta at the time I write this post) and 13.33, the results were the same with both versions. And on IOS 9.1 for the Cisco ASA side.
Configuration of the MX side
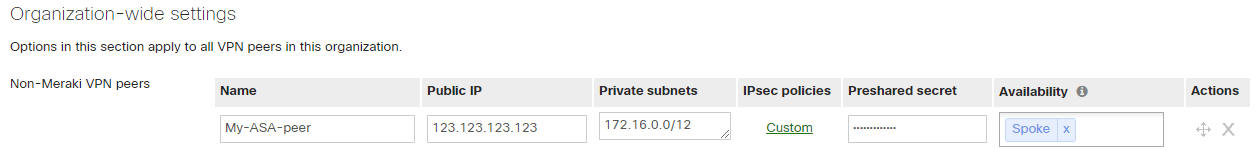
On the Meraki MX, the configuration for “Non-Meraki VPN peers” is under: Security Appliance > Site-to-site VPN > Organization-wide settings > Non-Meraki VPN peers.
Here you can give a name, the WAN IP of the VPN peer, the private subnets of the remote site, the IPSec policies for phases 1 and 2 the pre-shared secret key and the “Availability”.
The WAN IP, the private subnet and the pre-shared key do not need explanation.
IPSec Policies
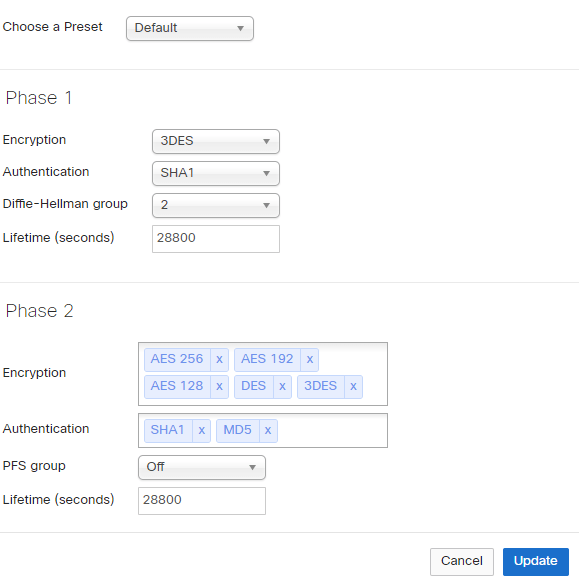
When you click on the IPSec policies, a popup appears with the Phase 1 and Phase 2 settings. You can choose between the “Default” settings, pre-set settings for AWS or Azure, or “custom” settings.
Here are the default settings:
(click on the image for a better view)
Of course, theses settings must match on the peer device.
Phase-1
For the ASA, the Phase-1 settings correspond to the crypto policy. You will find an example below.
Phase-2
For the phase-2, I experienced problems with the PFS between Cisco ASA and Meraki MX. The Meraki documentation recommend to disable PFS. It is still a security risk to disable PFS and it looks like a bug. Unfortunately, I have no more information on this point.
Availability
The availability setting on the MX is quite smart. As theses settings are valid for the entire organization, not only for the site or network, we can configure which MX unit in the organization will connect to this peer. For that, you can choose between “All networks” and in this case, all MX of your organization will connect to the peer, or you can set a specific network tag or set of tags. In this case, only the networks with this tag will connect to the peer. To tag networks, you must go to the Organization > Overview page, expand the table, select one or more network then click the “Tag” button to add or remove tags for the selected networks. For example, in a hub and spoke topology you can tag all the spokes with “spoke” and use this tag under the peer availability configuration.
Here is an example from the Dashboard:
(click on the image for a better view)
Configuration of the Cisco ASA side
Phase-1
Here is an example:
crypto ikev1 policy 100
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
Phase-2
For the phase-2, I experienced problems with the PFS between Cisco ASA and Meraki MX. The Meraki documentation recommend to disable PFS. It is still a security risk to disable PFS and it looks like a bug. Unfortunately, I have no more information on this point.
Another important point for the Phase-2 configuration on the ASA; the security association (SA) can have a lifetime in seconds and in data-volume on the ASA. But Meraki does not “understand” the data volume limit, so when that threshold is reached on the ASA side, before the lifetime runs out, the tunnel hangs for the remainder of the lifetime. I recommend to remove the volume limit from the ASA configuration or set it to unlimited.
Then, of course, the ACL must match on both ends and the SA lifetime timer too. If the timers do not correspond, the tunnel may come up, but this may cause problems explained here: https://www.ietf.org/proceedings/53/I-D/draft-ietf-ipsec-ike-lifetime-00.txt
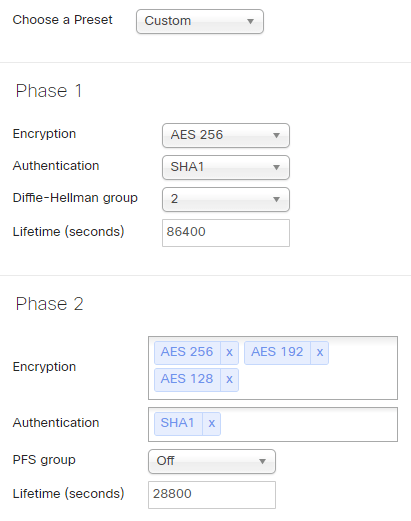
Here is a configuration example for ASA, tested with IOS 9.1:
access-list asa2mx extended permit ip object your-local-network-object object your-remote-network-object
!
crypto ipsec ikev1 transform-set MX-Transform-Set esp-aes esp-sha-hmac
!
crypto map mymx 100 match address asa2mx
crypto map mymx 100 set peer 123.123.123.123
crypto map mymx 100 set ikev1 transform-set MX-Transform-Set
crypto map mymx 100 set security-association lifetime seconds 28800
crypto map mymx 100 set security-association lifetime kilobytes unlimited
crypto map mymx interface outside
!
crypto ikev1 enable outside
!
The configuration above corresponds to this IPSec configuration on the MX:
(click on the image for a better view)
Good to know
Some tips from my experience:
- When you make a change on the MX “non-Meraki VPN Peers” and click on “Save”, the MX take all the existing tunnels down and start the negotiation again. Even your change was only on one specific peer, all tunnels are affected.
- If a tunnel hangs on the ASA side because your configuration does not match on both ends, the best is to manually clear the tunnel on the ASA once you changed the configuration. For this, enter this command on the ASA:
clear ipsec sa peer x.x.x.x
If you have other experiences on site-to-site VPN tunnels between Meraki MX and Cisco ASA or another vendor, please do not hesitate to add a comment below.
Hey @Larry DuBose
Can you please share the config for CSR. I am going to establish tunnel between MX and CSR soon.
I have activated site to site VPN from Meraki to ASA device. its works as well.
In Meraki i have 2 link. Primary link and Secondary link.
When my primary link down, then i use secondary link, but the VPN has not established. even My Secondary link already registered in ASA.
If i use primary link OK, but use secondary link Cannot connect.
Please your suggestion
Hi Shindy,
Thank you for your comment.
Well, it’s difficult to answer without knowing all the details.
What I can say is: try to see the debugging logs on the ASA side, because on the Meraki side the logging possibility is really not enough. Check the ASA logs of the VPN when using the second link, is it established or not, and why (authentication or source-IP problem maybe?), or is it established but routing is not working, etc.
Then, if it’s urgent and production is impacted, it’s probably better to contact Cisco TAC or Meraki support. 🙂
And if you solve the problem and it may interest the community, feel free to share the problem and the solution here, thank you.
Jerome
i had site to site VPN connection between ASA and Meraki.
When ASA as initiator tunnel is forming but when meraki as initiator its not forming the tunnel.
Can you please suggest what all possible reasons for it
Dear Sri,
I cannot tell you why, but try to enable the debugging on the ASA side when the Meraki is trying to form the tunnel.
You can also capture the traffic on the ASA WAN interface to see if the Meraki MX is really trying to establish the tunnel.
I hope it helps.
Best Regards,
Jerome
Hello Jerome,
I notice in your ‘good to know’ section you say the Non-Meraki peer VPN connections are reset every time a change is made.
I’m experiencing this when I make non-VPN firewall rule changes. Is this what you observed?
I have a case open with Meraki but perhaps it’s ‘expected behaviour’
Kind regards,
Gary .
Hi Gary,
Yes, when I was doing any change to the non-VPN firewall list (for example adding or removing a firewall) or to any rules of the non-VPN firewall, the VPN tunnels to ALL the non-Meraki firewalls made a reset. And sometimes, some of the tunnels made 5 to 10 minutes to be up again.
But, because having non-Meraki VPN tunnels was only during a migration phase, I did not opened any ticket for this. At the end of the project, I replaced all the non-Meraki firewall with Meraki MX.
I hope this helps.
Best Rgds,
Jerome
If I have several Meraki Sites and MX’s, will they all use the site-to-site tunnel if “Everyone” is selected in “Availability” .
MX to MX tunnels depends on Merki autovpn. For each site, you can configure if it’s a hub or spoke site.
If you configure a site with another site-to-site end point (a Cisco ASA or other), and you specify “everyone” in availability, then all the MXs will try to establish a tunnel to this site.
I hope this answers your question.
Best regards
Jerome
this corrected my issue between the Meraki and Cisco CSR1000. Just had to add the following and then restart the tunnel:
crypto map mymx 100 set security-association lifetime seconds 28800
crypto map mymx 100 set security-association lifetime kilobytes unlimited
Thank you very much for your comment Larry.
Best,
Jerome
vpn is up showing state is up. but traffic is not flowing between site to site.
lan to lan ping not working please suggest .
Well, it can be many things. And configuration may be a little different depending of the ASA version you have.
Check the ACLs, they must match traffic you want to pass through the tunnel.
Make a debug on the ASA side, to see the real state of the tunnel and if packets, and how many, are encrypted /decrypted.
On the MX side, you cannot see many details, but on the ASA side, the debug commands will help you a lot.
I hope this helps.
Jerome